Today I’ll tell you how do you hack any password protected wi-fi network with “CommView For Wi-Fi” software.
First you have to know what is Wi-Fi and how dose it work?
"Wi-Fi" is a type of wireless networking protocol that allows devices to communicate without cords or cables.
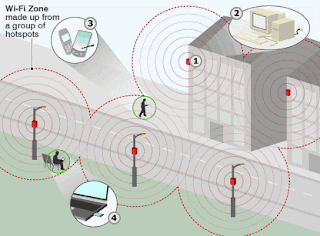
1: Wi-fi uses antennas around which wi-fi "hotspots" are created. The hotspots are outlets equipped to receive the radiowaves that power wireless networking. Until recently, wi-fi has been confined to more than 10,000 hot-spots in cafes, bars and airport lounges. But various projects are under way to set up city-wide zones, where a series of antennas are installed in the streets, on lampposts or street signs. The hotspots around them together create a much wider area of coverage. Norwich has a mesh network which links each lamppost antenna to the next creating a seamless wi-fi hotspot around the centre of the city.
2: The source internet connection is provided by a PC or server to which the antennas are connected either wirelessly or via a cable.
3: Some mobile phones and personal digital assistants (PDA) now have wi-fi chips installed. With mobile phones, this means conventional networks can be bypassed and inexpensive long-distance calls made over the web (using Voice over Internet Protocol, VoIP).
4: Many laptops and handheld computers now come with built-in wi-fi connectivity; it is also possible to add wi-fi to your computer with a special card that plugs into a port on your laptop.
Some organizations provide it for free but maximums provide it for business purpose only. And you have to give a password to access this kind of network.
This software price is $1099. Don't worry, I'm giving you for FREE.
Download This Software from
HERE.
Note: Please turn off your anti-virus program before you install this software, otherwise this software will not work properly. After completing installing process you can re-run your anti-virus program.
Now follow the Instructions bellow:
1. Install the software and drivers.
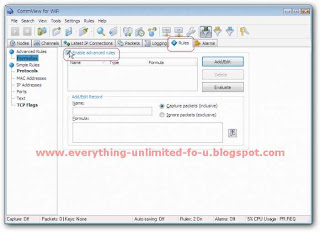
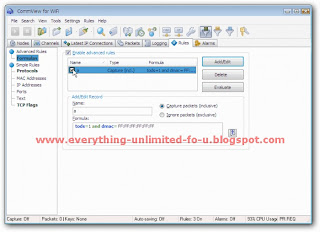
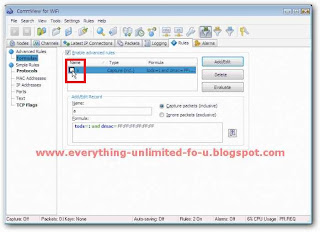
2. Click on ‘Rules’ tab and tick on ‘Enable advance rules’ option.
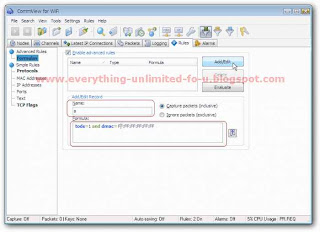
3. Type ‘a’ on Name box and Past this code on formula box “tods=1 and dmac=FF:FF:FF:FF:FF:FF” like picture bellow. Then click ‘add/edit’ button.
4. A window will appear like the picture bellow. Give a tick on ‘a’ .
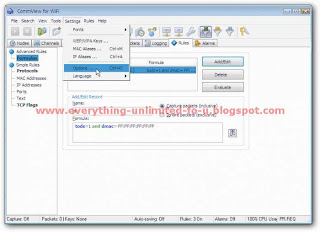
5. Then go to ‘Settings’ and click ‘Option’
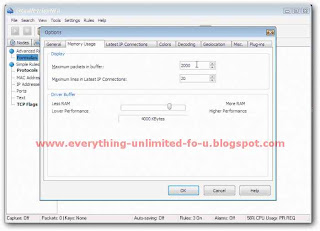
6. Go to ‘Memory Usage’ tab and set everything just like this picture & click ‘Ok’ (Restart may be required).
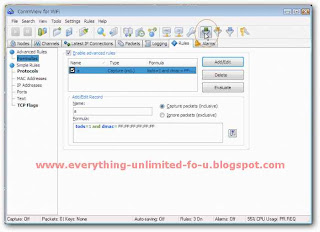
7. Check ‘D’ funnel and uncheck another two funnel from the right top of this window.
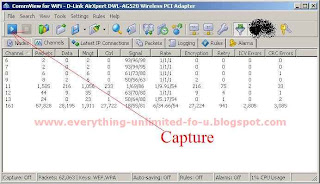
8. Click ‘Search’ button and find the network that you want to creak.
9. Then drag it on ‘Channel’ tab and click ‘Capture’ button.
10. Now which one is do not capturing anything give it to password protected network and connect it. When it will ask for password, give any as you wish.
11. It will show this massage “Connected with limited connectivity”.
(I have no Wi-Fi connections at this time. that is why, I can’t share some screenshots).
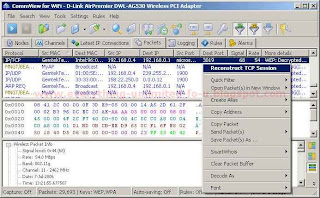
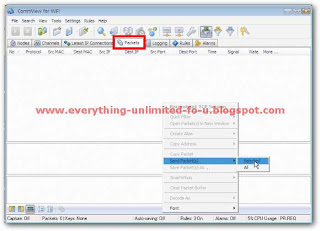
12. Click on main menu again and then click on ‘Packets’ Tab. If everything was all right, you will see some Couple of Packets.
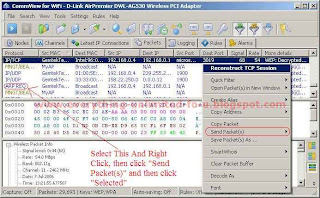
13. Click right button on “ARP REQ” Packet and then > “Send Packet(s)” > Selected.
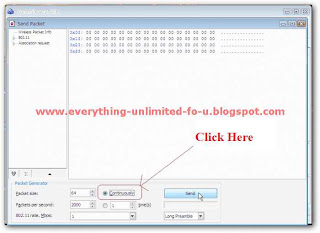
14. This menu will appear.
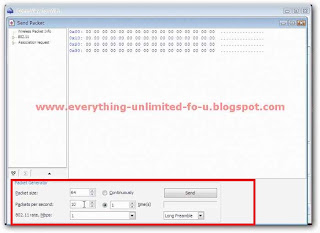
15. Now change all values just like this and click ‘Send’.
16. Go to ‘Rules’ Tab again and uncheck the Rules “a” .
17. Select first 20000 packets and save it. Make sure you are saving it as “dump cap” file in place of “ncf” file format. (I have no Wi-Fi connections this time, that is why I can’t share some screenshots).
18. Now download a zip folder named “Aircrack-NG” from
HERE. And extract it.
19. Open ‘bin’ folder and run this file ‘aircrack-ng-GUI.exe’. Then go where you saved the packets, select all and click launch.
20. An ‘IV’ list will came. Select the network that you want to creak.
21. Click ‘Connect’. You will be connected with your desire network like a magic !
22. Enjoy the Unlimited Wi-Fi Internet.
Also you can do with this software :
You can find more tutorials on about this software on the help menu of this software.
If you have any suggestion or comment please feel free to post it on the box bellow !








 Download
Download



![[Image: 001cv.png]](http://img838.imageshack.us/img838/300/001cv.png)
![[Image: 002rg.png]](http://img836.imageshack.us/img836/1907/002rg.png)
![[Image: 003bd.png]](http://img834.imageshack.us/img834/7643/003bd.png)
![[Image: 004k.png]](http://img217.imageshack.us/img217/3421/004k.png)
![[Image: 005hy.png]](http://img29.imageshack.us/img29/7562/005hy.png)
![[Image: 006fj.png]](http://img691.imageshack.us/img691/1796/006fj.png)
![[Image: 007pa.png]](http://img576.imageshack.us/img576/1710/007pa.png)
![[Image: 008bo.png]](http://img291.imageshack.us/img291/8648/008bo.png)
![[Image: 009kw.png]](http://img707.imageshack.us/img707/8946/009kw.png)